Information Security Policies
1. Objectives
To strengthen the information security management of MACHVISION Inc Co., LTD (hereinafter referred to as “our company”), and assure the confidentiality, integrity, and availability of all assets and information, meet the requirements of relevant laws and regulations, protect them from deliberate or unexpected internal and external threats, the policy is therefore established.
2. Scope of application
(1)The scope of application of this policy covers all employees of our company, outsourced companies, and visitors, etc.
(2)The scope of information security management covers the following areas, to prevent any possible risk and danger from improper use, leak, tampering, and destruction of information due to human errors, deliberate damage or natural disasters, etc. The management items are as follows:
a. Establishment and evaluation of information security policies.
b. Establishment and operation of the information security organization.
c. Classification, rating, and control of information assets.
d. Management of information security risks.
e. Personnel security management and education and training.
f. Physical and environmental security.
g. Communication and operation security management.
h. Access control security.
i. Compliance of unit policies to relevant legal regulations.
3. Goals
To assure the confidentiality, integrity, and availability of our company's assets, and protect the security of user data privacy. All employees of our company make efforts together to achieve the following goals:
(1)Protect the security of information of our company's R&D, business, production, and services, and assure that the information can only be accessed by authorized personnel to protect its confidentiality.
(2)Protect the security of information of our company's R&D, business, production, and services, and prevent unauthorized modification to ensure accuracy and integrity.
(3)Ensure that the implementation of all our company's operations and services comply with the requirements of relevant laws and regulations.
4. The organization for Information Security
The Company has established an information security management committee, with the top head of the information department as the committee chairman, and is composed of network service members who implement the information security plans. The committee is responsible for external information risk assessment and resource introduction assistance, information security system establishment, information security supervision and audit, and continuous enhancement of information security concepts and awareness.
5. Information security measures
6. Continuous improvement framework
The still maintain PDCA (Plan-Do-Check-Act) cyclic management mode to ensure the attainment of goals and continuous improvement
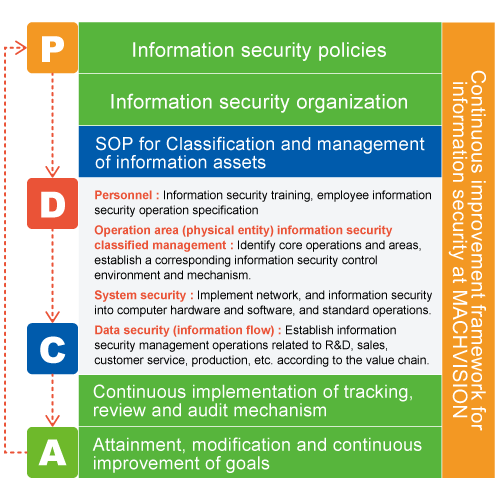
At the end of 2023, Taiwan Stock Exchange assisted public companies with improvement on information security and management, using “Information Security Management and Control Guidelines for Public Companies” as the foundation of corporate improvement cycle.
7. Implementation and status of information security
MACHVISION is a team based on IT research and development, so it especially emphasizes and maintains the key competitiveness of research and development, in addition to the anti-virus and anti-hacking protective measures for software and hardware that many other companies have implemented.
As of 2021, the implementation of three-level information security has been completed, as described below:
(1)Data encryption management:All company data files, graphics files, and software programs are encrypted and managed. If any report and data related to customer and supplier is needed, it requires the application for approval and decryption. Only in this way, external customers and suppliers can read the report, to enable the attainment of business activities and provision of related services from the suppliers.
(2)Strengthen information security in user environment: Currently, the R&D Department of high-level information security area is restricted to personal processing information equipment. All external computers and hardware equipment can be carried inside with restriction from connecting to the internal environment of MACHVISION. Moreover, personal processing computers will be blocked from us due to improper operations. With the control of USB use in the company, since the sales and customer service will inevitably need assistance from data analysis, the Information Department installs public virus scanning computers at all floors for users to scan data for viruses before loading.
(3)Establishment of internal antivirus software and external firewall antivirus/anti-hacking.
Recently, many large companies have suffered from malicious software and computer virus attacks, which are in a complicated situation. The awareness of information security protection continues to increase. With the training and real-time assistance from the frontline information security companies, it reduces the risk of MACHVISION’s commitment to customers and shareholders and the adverse effects on operational results, finance, and prospects.
(4)Supporting and backup mechanism: Execute the upgrade of the critical server system to high reliability, and incorporate the upgrade and improvement on the virtual server model and backup server. Develop and execute the configuration of full backup on the computers of senior managers to reduce the risks of data loss caused by malicious software and computer virus attacks.
(5)Introduction of email filtering services: The introduction of cloud email filtering services will reduce the risks of related email attacks.
(6)Establishing the management architecture of server status: Establish logs management and monitor the server service and resources status.
(7)Conduct vulnerability scanning and social engineering drills to assess internal and external environmental risks and strengthen social engineering awareness training.
(8)Implement firewall-based external network traffic monitoring and alert management mechanisms for enhanced cybersecurity control.
8. Information Security Risk Management Organization
The Company establishes the Risk Management Committee targeting risks related to information security. The chief of the IT Department serves as the convener while the network service members participating in the actual execution of information security projects form the Committee members. One dedicated information security supervisor and one dedicated personnel are assigned to take charge of the establishment of the information security system, technical introduction, and information security supervision and auditing through cooperation with colleagues from the IT Department.
The Committee conducts risk analysis on the information security and internet risk assessment procedures based on the level of risk effect and probability of occurrence. The Committee also conducts corresponding management mechanisms for high-risk environments and systems to establish the high-reliability model, data backup architecture, and remote backup model, which will reduce the impact of information security events.
The Committee formulates and regularly reviews the information security policies in addition to reporting the information security event reporting and response mechanism on the monthly information security report and anomalies review meeting. The Committee also reports the information security checks to the Board of Directors.
The last assessment report issued by the Committee is dated December 19, 2024, as shown in the annual information security report:
(1) Conclusion of 2023 information security monthly reports: Explanation on the information security management items and management anomaly events. The number of major anomaly events for 2024 is 0.
(2) Supplements to key information security management: Endpoint virus attacks and blocking records, internet and server anomaly records, external attacks detection and blocking records. Reporting on the upgrade plans of related network equipment.
(3) Guide to information security and internet management strengthening: The guide takes consideration of the 2024 information security strengthening guide from the sustainability report. In particular, the mandate to professional third-party for information security audit and diagnosis and the drills of social engineering was completed for the first half of the year. The internal advocacy and educational training for information security were also implemented in all employees.
During the meeting, it was required to strengthen the filtering and protection of junk email/phishing websites/email attacks and build up voluntary management of information security messages and management of high-risk and high-severity attacks.




